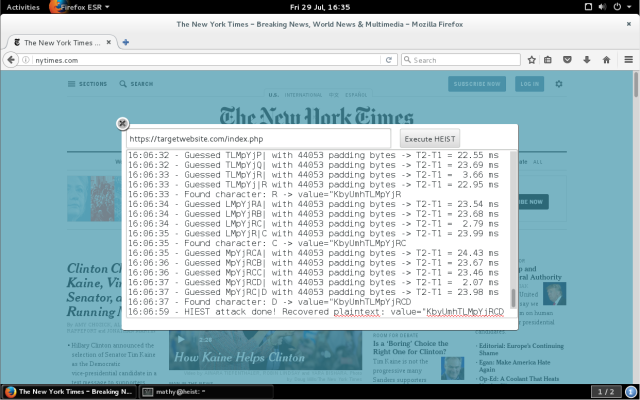
Approach exploits how HTTPS responses are delivered over transmission control protocol.

BlackBerry’s last two smartphones have been Android-powered devices featuring a suite of BlackBerry apps for communication, security, time management, and other functions. Now you don’t need a BlackBerry phone to use some of those apps anymore.
The company has released BlackBerry Hub+ for Android, which brings BlackBerry’s unified messaging app as well as its calendar and Password Keeper apps to any phone running Android 6.0 or later.
To use the apps, you just need to download and install BlackBerry Hub and BlackBerry Services from the Google Play Store.
Continue reading BlackBerry launches Hub+ suite of apps for Android at Liliputing.


BlackBerry’s last two smartphones have been Android-powered devices featuring a suite of BlackBerry apps for communication, security, time management, and other functions. Now you don’t need a BlackBerry phone to use some of those apps anymore.
The company has released BlackBerry Hub+ for Android, which brings BlackBerry’s unified messaging app as well as its calendar and Password Keeper apps to any phone running Android 6.0 or later.
To use the apps, you just need to download and install BlackBerry Hub and BlackBerry Services from the Google Play Store.
Continue reading BlackBerry launches Hub+ suite of apps for Android at Liliputing.

Groups rejecting climate science see some success in FOIA efforts.
Neurons that talk to each other have proteins that mirror each other.
Vom Dorf bis zu den Pyramiden: In Civilization 6 kämpfen wir uns erneut durch die Geschichte – aber sehen dank neuer Funktionen mehr davon. Golem.de hat eine frühe Version des Strategiespiels ausprobiert. (Civilization, Games) 

Vom Dorf bis zu den Pyramiden: In Civilization 6 kämpfen wir uns erneut durch die Geschichte - aber sehen dank neuer Funktionen mehr davon. Golem.de hat eine frühe Version des Strategiespiels ausprobiert. (
Civilization,
Games)

Mit dem Projekt CSX will ZTE seine Nutzer in den Produktionsprozess eines neuen mobilen Devices einbinden. CSX steht dabei für “Crowd Sourced X” – wobei das X für alles stehen kann, was ZTE realistisch gesehen produzieren kann. 2017 soll das Gerät auf den Markt kommen. (ZTE, Smartphone) 

Mit dem Projekt CSX will ZTE seine Nutzer in den Produktionsprozess eines neuen mobilen Devices einbinden. CSX steht dabei für "Crowd Sourced X" - wobei das X für alles stehen kann, was ZTE realistisch gesehen produzieren kann. 2017 soll das Gerät auf den Markt kommen. (
ZTE,
Smartphone)

Die aktuelle Version 5.2 der freien Officesuite Libreoffice unterstützt den TSCP-Standard für Geheimhaltungsstufen. Verbessert hat das Team zudem die Interoperabilität und die Arbeit mit Dokumenten soll dank einer kleineren Werkzeugleiste leichter sein. (Libreoffice, Document Foundation) 

Die aktuelle Version 5.2 der freien Officesuite Libreoffice unterstützt den TSCP-Standard für Geheimhaltungsstufen. Verbessert hat das Team zudem die Interoperabilität und die Arbeit mit Dokumenten soll dank einer kleineren Werkzeugleiste leichter sein. (
Libreoffice,
Document Foundation)

Many investors holding BTC sell holdings in wake of Bitfinex hack.
Die Deutsche Umwelthilfe findet die Rücksendung von Elektroaltgeräten per Post nicht besonders umweltfreundlich. Dennoch kritisiert sie die Praxis von Amazon scharf, die Kunden über dieses neue Recht falsch zu informieren. (Recycling, Amazon) 

Die Deutsche Umwelthilfe findet die Rücksendung von Elektroaltgeräten per Post nicht besonders umweltfreundlich. Dennoch kritisiert sie die Praxis von Amazon scharf, die Kunden über dieses neue Recht falsch zu informieren. (
Recycling,
Amazon)


Earlier this year ZTE announced plans to launch a crowdsourced smartphone. Now the Chinese phone maker is kicking things off by launching Project CSX, a community forum where potential customers will be able to share their ideas for a smartphone that ZTE hopes to bring to market in 2017.
Anyone can join the community by visiting community.zteusa.com to sign up.
ZTE says it Projcet CSX is “a new method for developing products that engages directly with consumers at every step of the development process.”
Uses will be invited to submit ideas and then vote on their favorites.
Continue reading ZTE launches Project CSX: will release a crowdsourced phone in 2017 at Liliputing.


Earlier this year ZTE announced plans to launch a crowdsourced smartphone. Now the Chinese phone maker is kicking things off by launching Project CSX, a community forum where potential customers will be able to share their ideas for a smartphone that ZTE hopes to bring to market in 2017.
Anyone can join the community by visiting community.zteusa.com to sign up.
ZTE says it Projcet CSX is “a new method for developing products that engages directly with consumers at every step of the development process.”
Uses will be invited to submit ideas and then vote on their favorites.
Continue reading ZTE launches Project CSX: will release a crowdsourced phone in 2017 at Liliputing.




 Vom Dorf bis zu den Pyramiden: In Civilization 6 kämpfen wir uns erneut durch die Geschichte - aber sehen dank neuer Funktionen mehr davon. Golem.de hat eine frühe Version des Strategiespiels ausprobiert. (
Vom Dorf bis zu den Pyramiden: In Civilization 6 kämpfen wir uns erneut durch die Geschichte - aber sehen dank neuer Funktionen mehr davon. Golem.de hat eine frühe Version des Strategiespiels ausprobiert. ( Mit dem Projekt CSX will ZTE seine Nutzer in den Produktionsprozess eines neuen mobilen Devices einbinden. CSX steht dabei für "Crowd Sourced X" - wobei das X für alles stehen kann, was ZTE realistisch gesehen produzieren kann. 2017 soll das Gerät auf den Markt kommen. (
Mit dem Projekt CSX will ZTE seine Nutzer in den Produktionsprozess eines neuen mobilen Devices einbinden. CSX steht dabei für "Crowd Sourced X" - wobei das X für alles stehen kann, was ZTE realistisch gesehen produzieren kann. 2017 soll das Gerät auf den Markt kommen. ( Die aktuelle Version 5.2 der freien Officesuite Libreoffice unterstützt den TSCP-Standard für Geheimhaltungsstufen. Verbessert hat das Team zudem die Interoperabilität und die Arbeit mit Dokumenten soll dank einer kleineren Werkzeugleiste leichter sein. (
Die aktuelle Version 5.2 der freien Officesuite Libreoffice unterstützt den TSCP-Standard für Geheimhaltungsstufen. Verbessert hat das Team zudem die Interoperabilität und die Arbeit mit Dokumenten soll dank einer kleineren Werkzeugleiste leichter sein. (
 Die Deutsche Umwelthilfe findet die Rücksendung von Elektroaltgeräten per Post nicht besonders umweltfreundlich. Dennoch kritisiert sie die Praxis von Amazon scharf, die Kunden über dieses neue Recht falsch zu informieren. (
Die Deutsche Umwelthilfe findet die Rücksendung von Elektroaltgeräten per Post nicht besonders umweltfreundlich. Dennoch kritisiert sie die Praxis von Amazon scharf, die Kunden über dieses neue Recht falsch zu informieren. (