The secrets of the environment settings
If you look at aerial imagery of a region every day for a year, it never changes. Yet if you would fly over the same region in reality every day, it would almost never look the same twice. In reality, nature is a dynamically changing environment, and what you see from a cockpit reflects this.
Some of these changes have to do with weather – on a cloudy day, the light is different from bright sun, the shadows are muted, the amount of haze may change so that faraway terrain looks fainter… and these are readily captured by the weather simulation.
Yet there are more subtle effects. For instance, snow may linger on the ground even on a sunny day with temperatures above freezing if the original layer was thick enough. Snow may fall, but not remain on the ground if the ground is warm enough. In essence, whether you see snow or not depends not so much on how the weather is now, but how it has been the last days, weeks or even months.
Such changes to the scenery in FG are taken care of by the environment settings which control how the terrain is shown. You can find the menu as an entry under Environment.
Currently, the full range of environment effects is only implemented for the Atmospheric Light Scattering (ALS) framework starting from medium quality settings, however the snow effect is available for all rendering frameworks.
Let’s explore some of the things this can do:
Seasonal changes
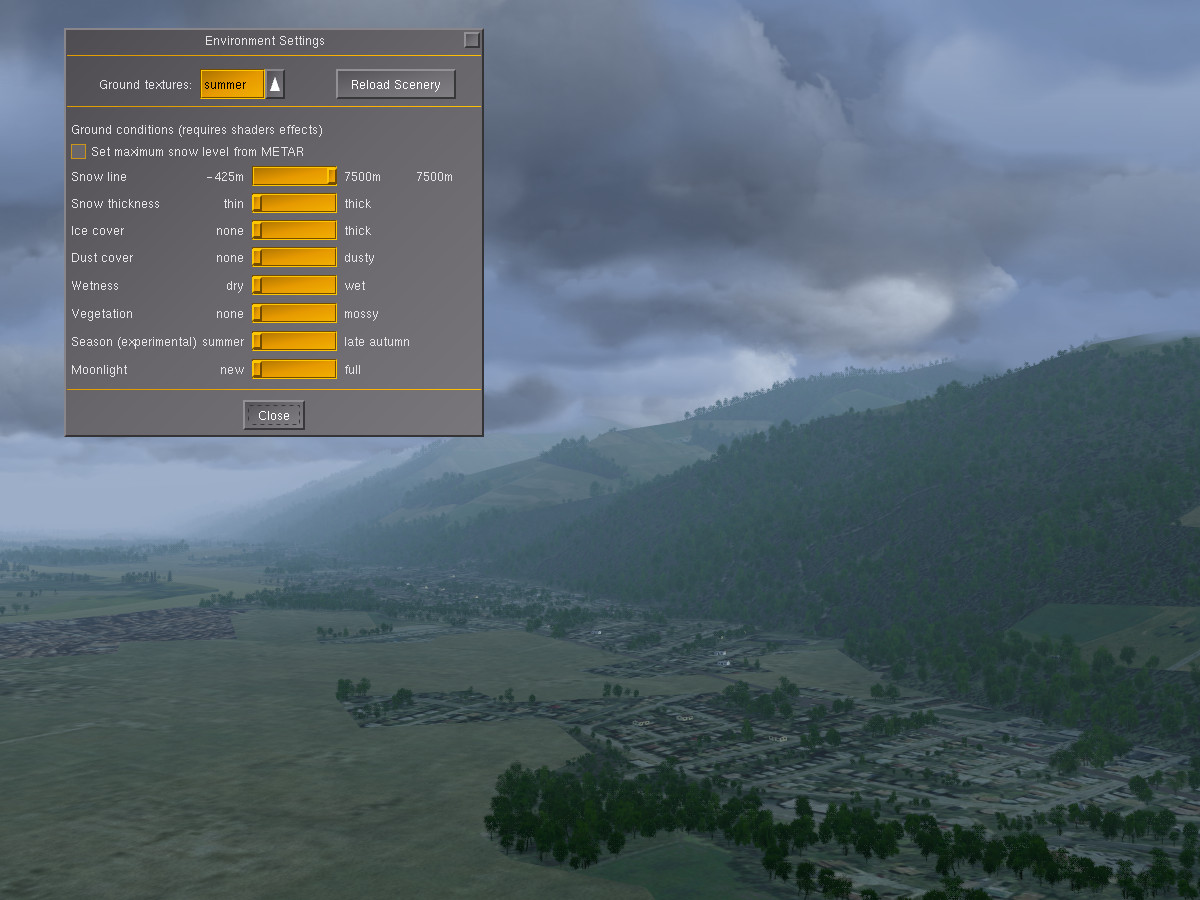
This is how the default terrain is shown without any environment effects – a summer day in Grenoble:
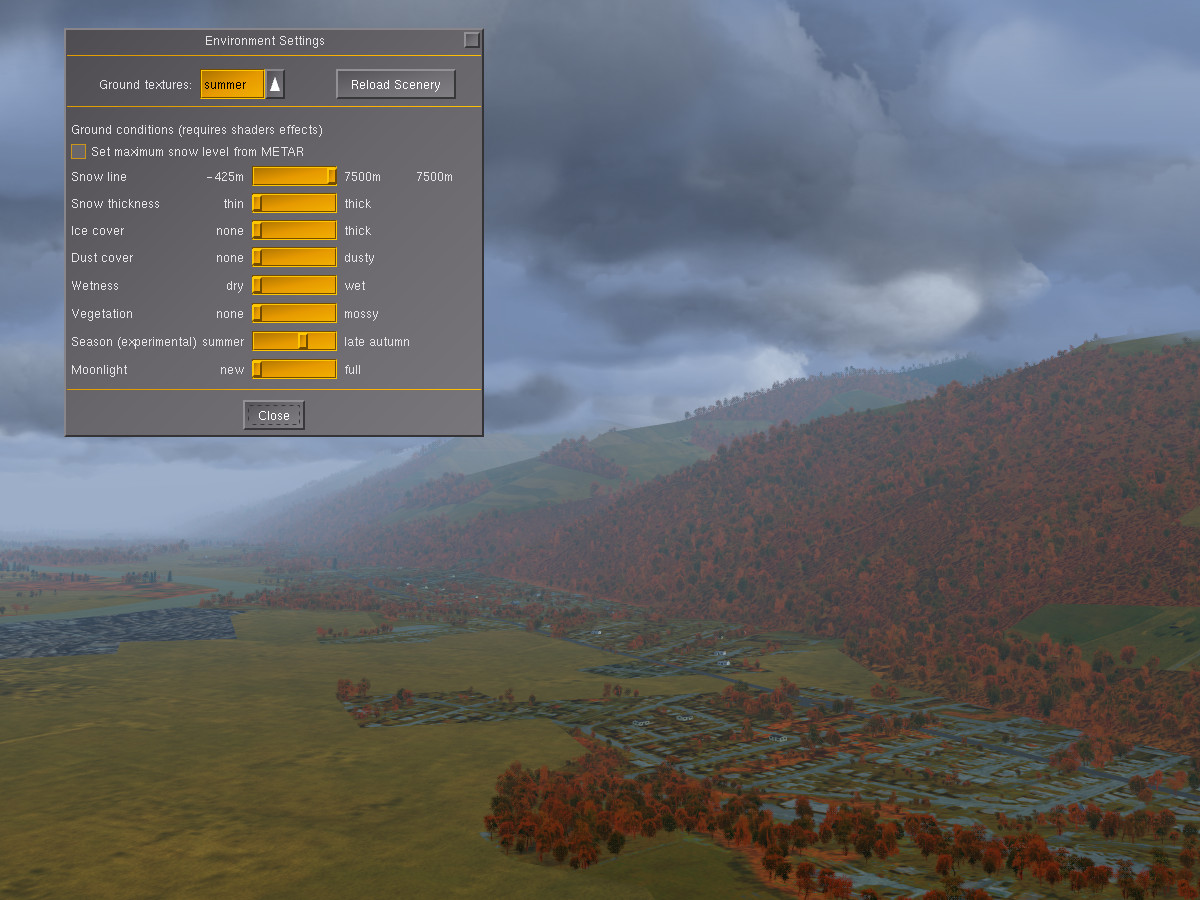
Moving the season slider somewhat to the right brings autumn coloring into the scene – deciduous tree patches change colors to orange-red, fields and grass appear yellowish:
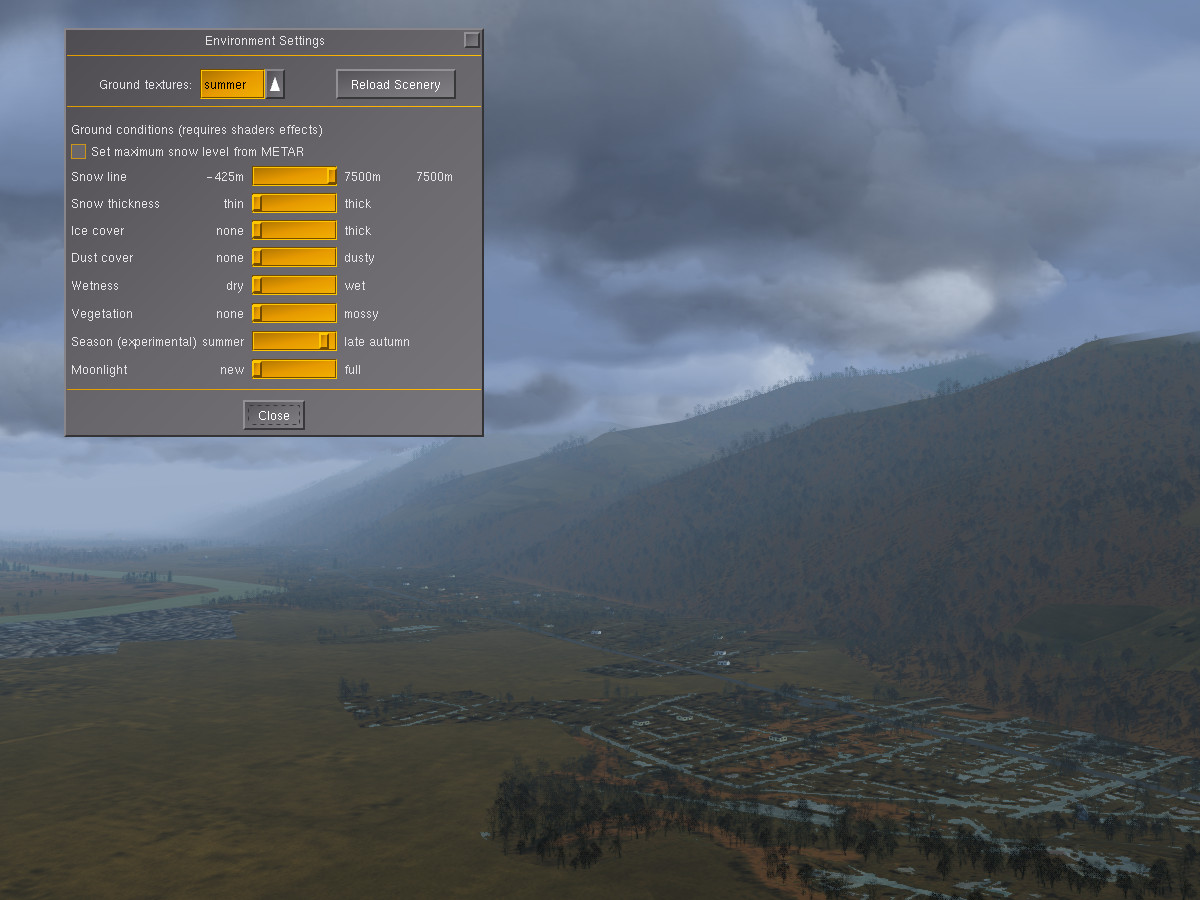
Changing to a yet later season causes deciduous trees to shed leaves and changes most of the vegetation to a dull brown:
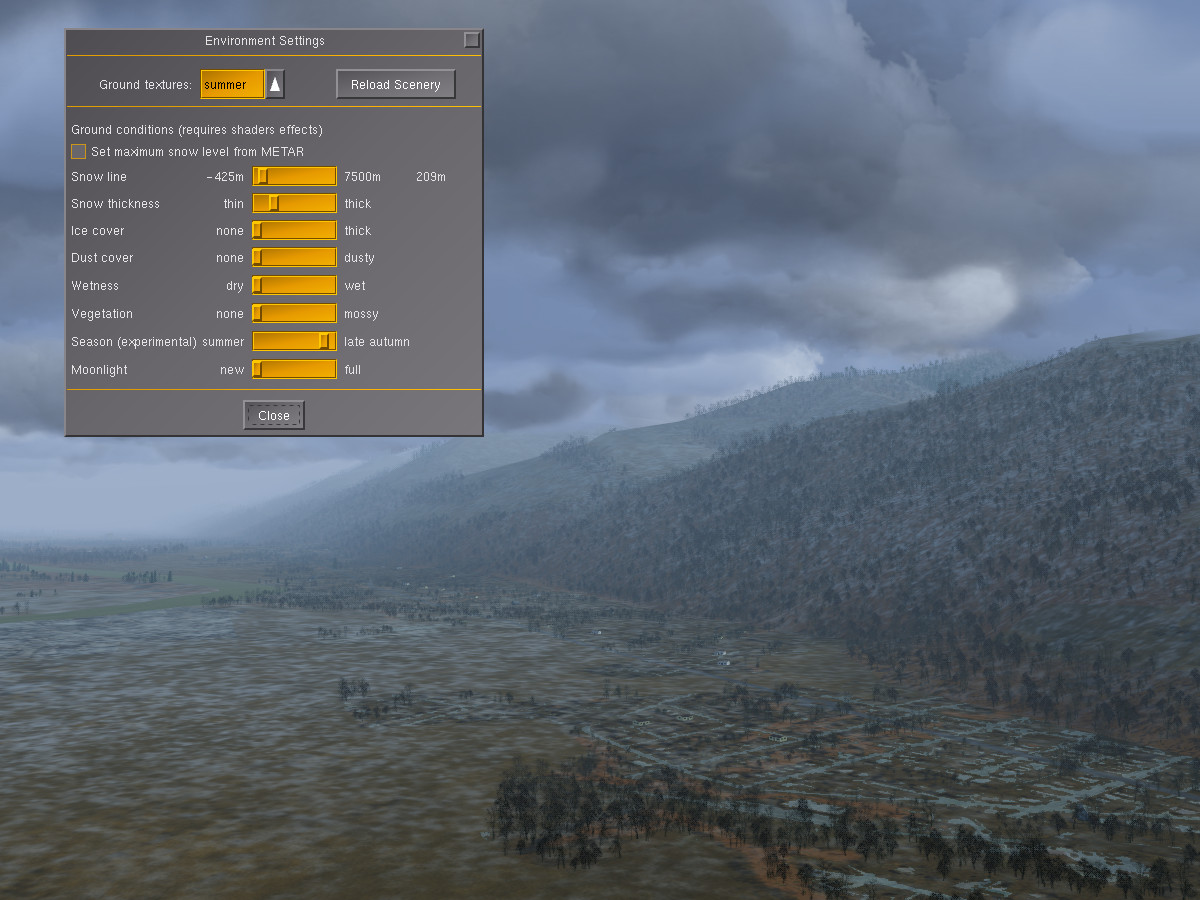
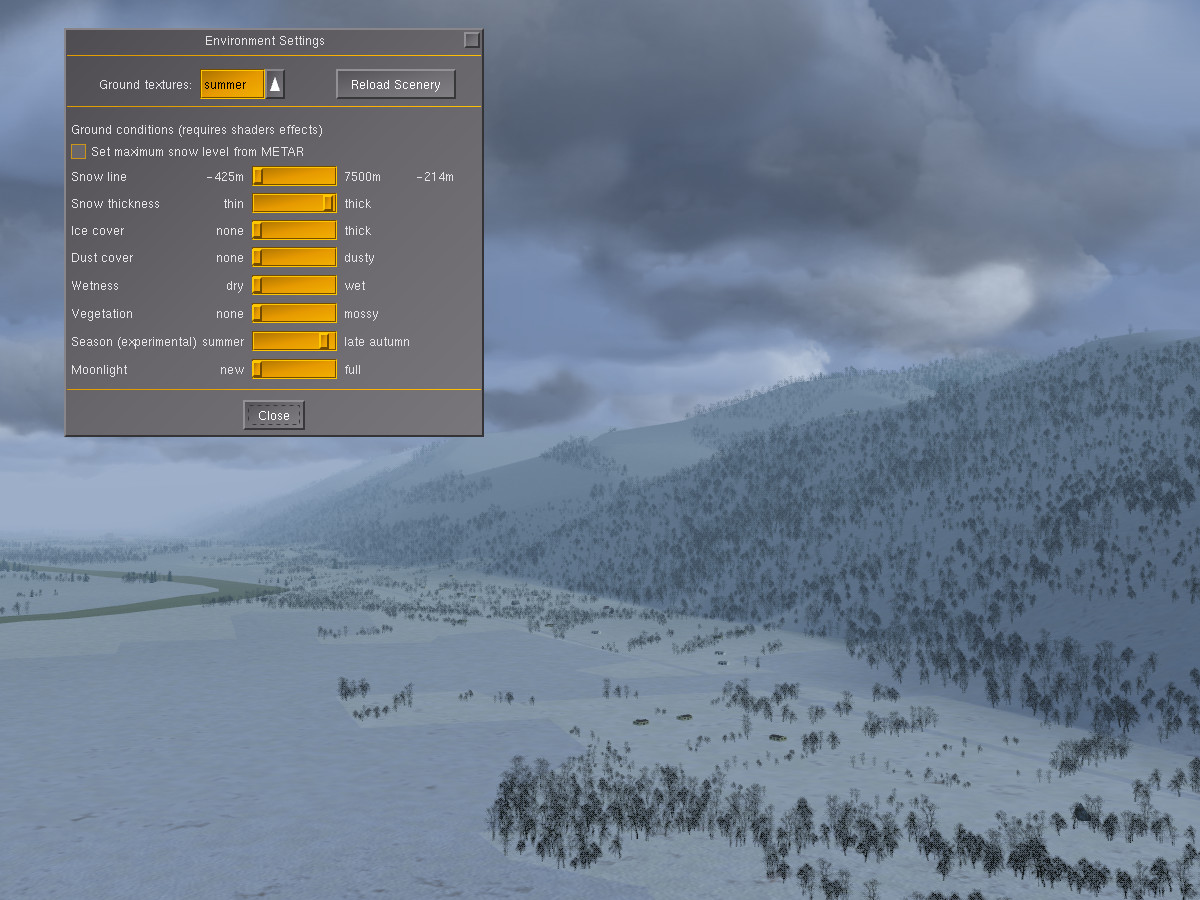
Modifying the snow line and thickness allows to add a sprinkle of snow to the valleys, simulating the first snowfall of late fall:
Finally, adding more snow changes the whole scene into deep winter:
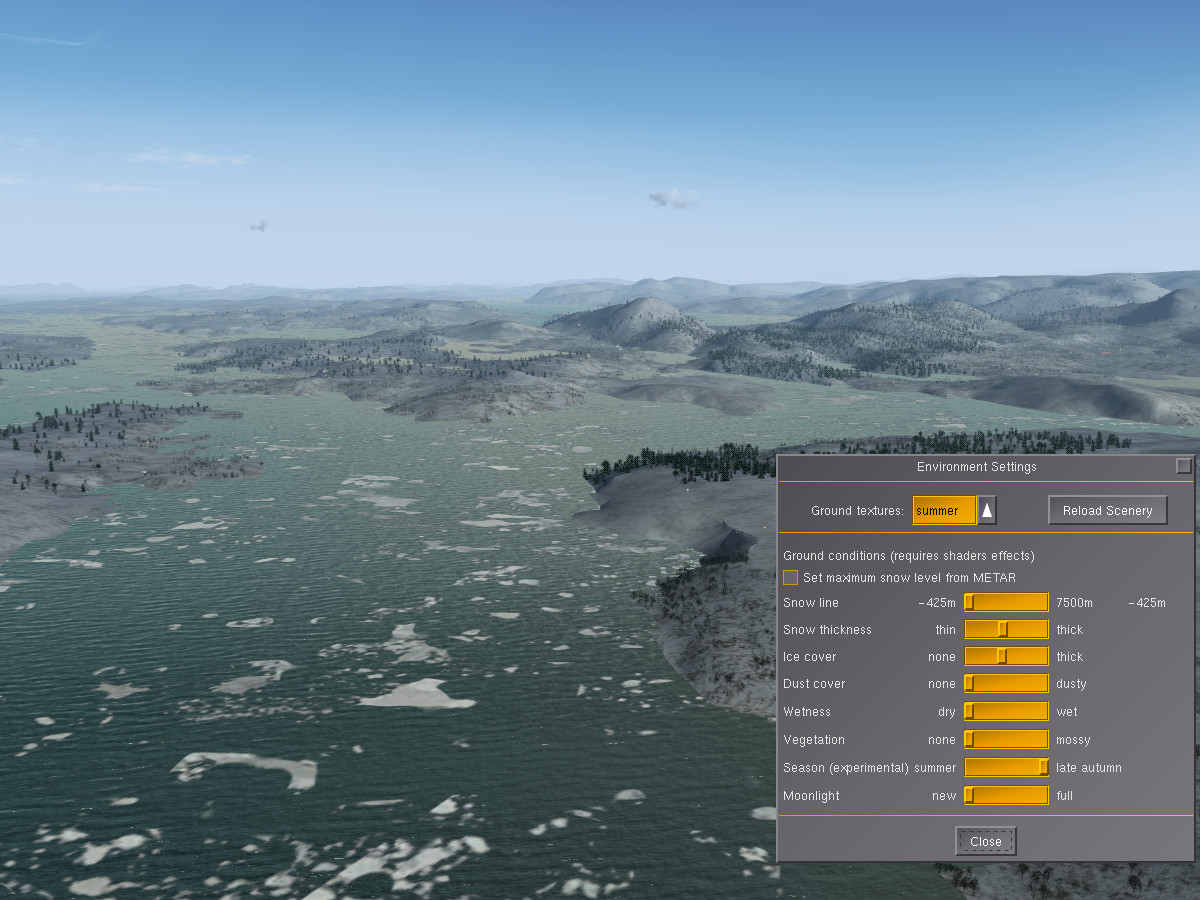
In coastal regions, the appearance of water can also be changed. Here is the coast of Norway near Bergen in summer:
Using the snow and ice sliders allows to simulate winter with lots of drift ice in the sea:
Using a combination of the season and snow settings, it is hence possible to simulate a lot of the seasonal changes during the year. But that’s not all.
Dust and greenery
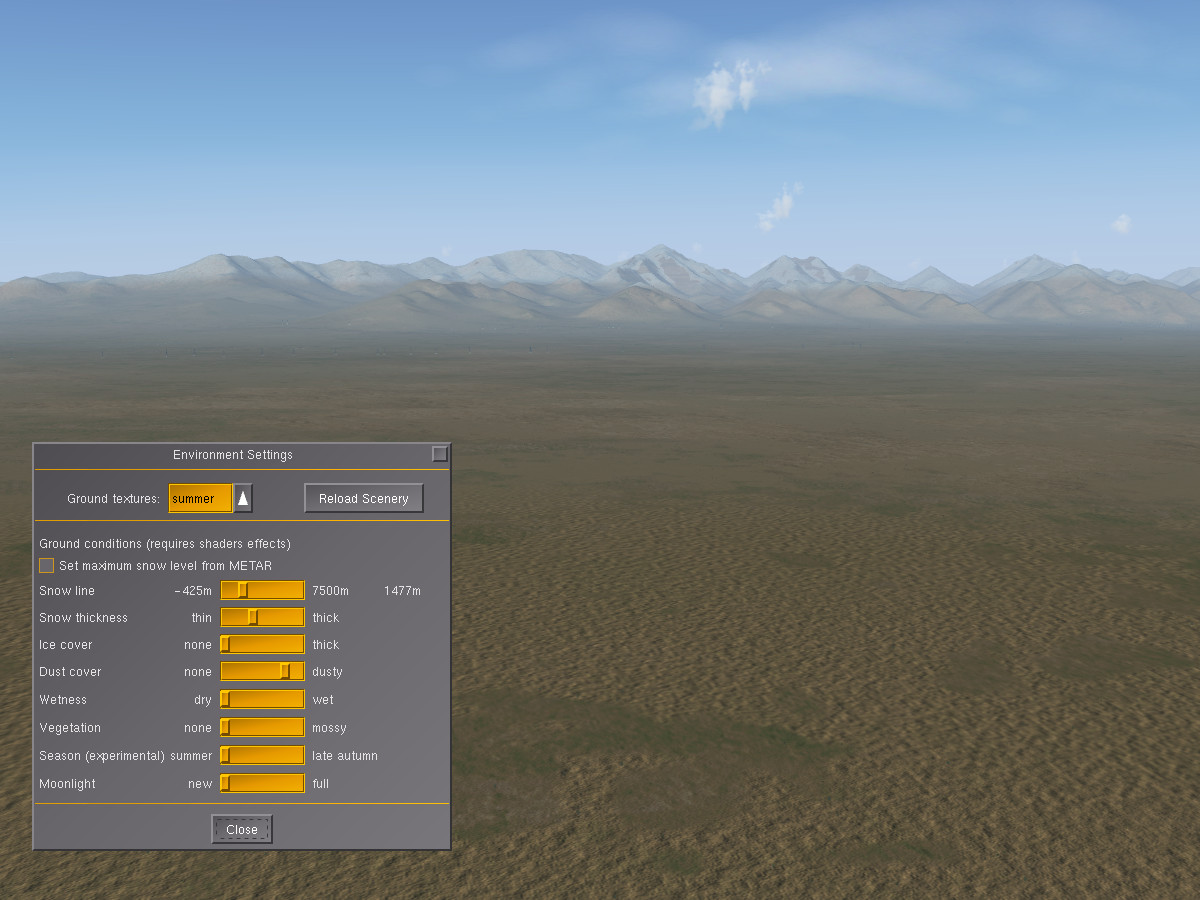
Have you noticed how colors fade during a long spell of dry weather, to be restored only when rain washes the dust away? Or how a desert might look green for a few weeks after rainfall, to change to its usual dusty appearance later? The environment system also provides those options – let us take a look at the Sierra Nevada. This is how the chain appears from China Lake (with a good measure of snow added to the peaks):
Using the dust slider makes all the colors fade and lets the scene appear dry:
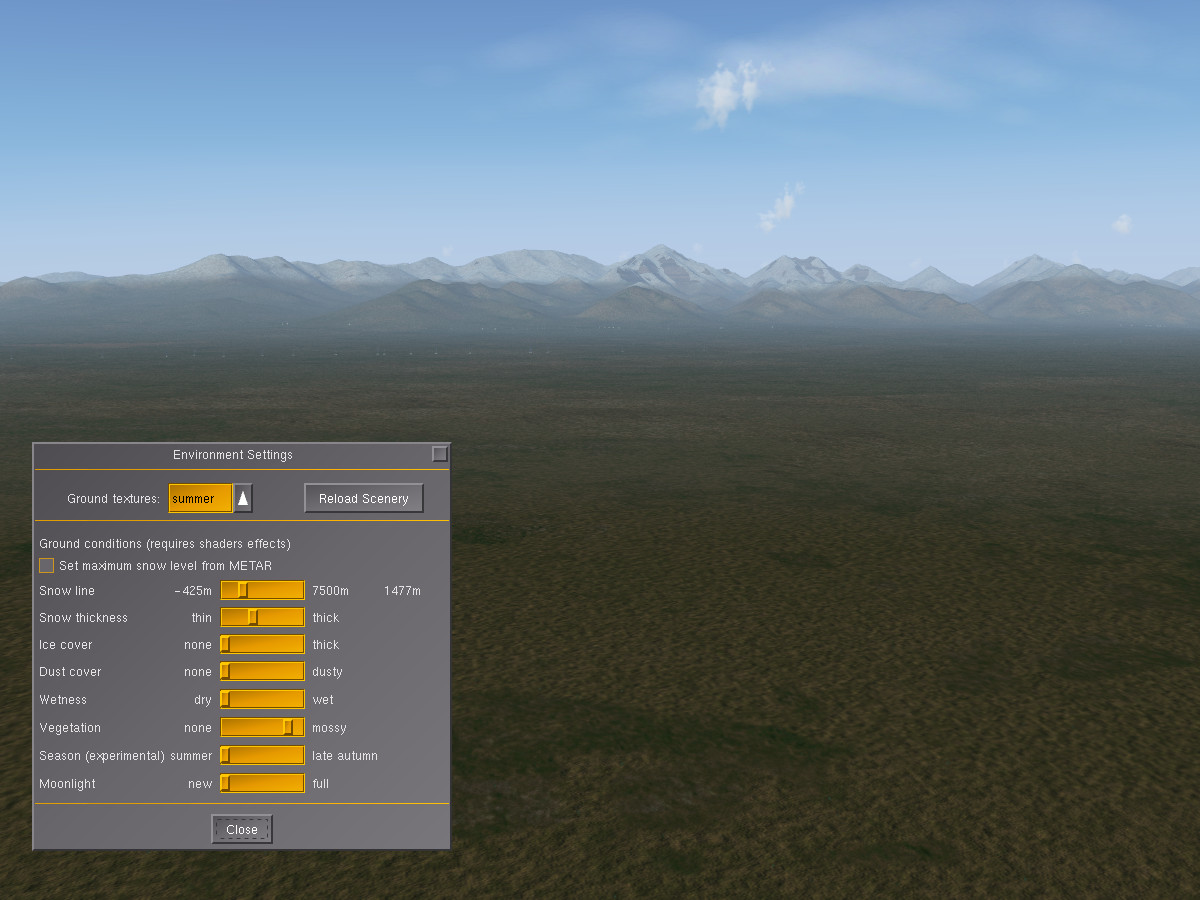
Using the vegetation slider instead gives a fresh green touch to the desert as if after a rainfall:
Changes may be subtle and affect more than just color. Consider this close-up of a dry runway:
The environment settings allow to make it wet (this will happen automatically when the weather predicts rain, but terrain can be wet without current rainfall). This creates puddles and alters the whole reflectivity of the surface – look at how the light changes:
Finally, adding snow covers the runway partially in snowdrifts:
Why can’t this happen automatically?
The environment subsystem just renders as it is told, it is hence easy to misuse it – think snowfall and ice cover on Caribbean islands for instance. Sometimes, the question gets asked why this is implemented that way, and why parameters aren’t just set automatically.
The answer to that is – based on what should they be set? Flightgear does not include a global climate simulation as would be needed to determine how likely it was that there was e.g. snowfall during the last days or weeks, or that there was a dry summer and hence everything should look dusty.
The idea is that the user can adjust these settings, either based on how the scene currently looks at a location, or based on what the user wants to experience (it’s a simulation after all – there’s nothing wrong with simulating a tropical day in Hawaii on a bleak winter day).
If used with some care, the environment settings offer a chance to experience the same scenery in a hundred different ways, each time subtly different.
If misused, the settings deliver weird to crazy results of course.
For the sake of completeness, for low-performance systems which are unable to run shader effects, using the commandline option –season=winter offers at least the choice between the default summer textures and a snow-covered set of textures, although no control over snowline and thickness.