2 more images in gallery
There has been a lot of ingenuity poured into creating crypto-ransomware, the money-making malware that has become the scourge of hospitals, businesses, and home users over the past year. But none of that ingenuity applies to Ranscam, a new ransom malware reported by Cisco's Talos Security Intelligence and Research Group.
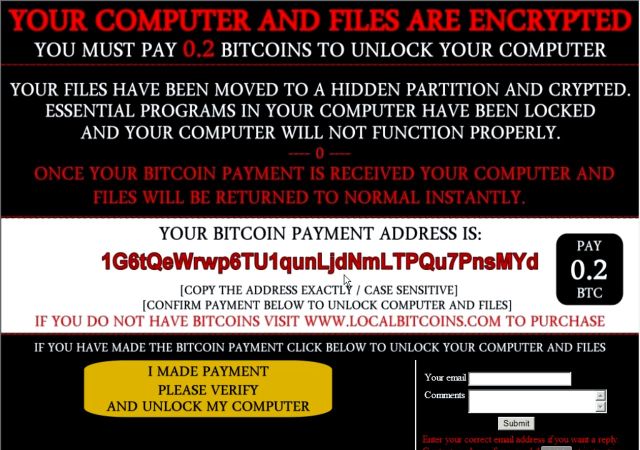
Ranscam is a purely amateur attempt to cash in on the cryptoransomware trend that demands payment for "encrypted" files that were actually just plain deleted by a batch command. "Once it executes, it, it pops up a ransom message looking like any other ransomware," Earl Carter, security research engineer at Cisco Talos, told Ars. "But then what happens is it forces a reboot, and it just deletes all the files. It doesn't try to encrypt anything—it just deletes them all."
Talos discovered the file on the systems of a small number of customers. In every case, the malware presented exactly the same message, including the same Bitcoin wallet address. The victim is instructed: