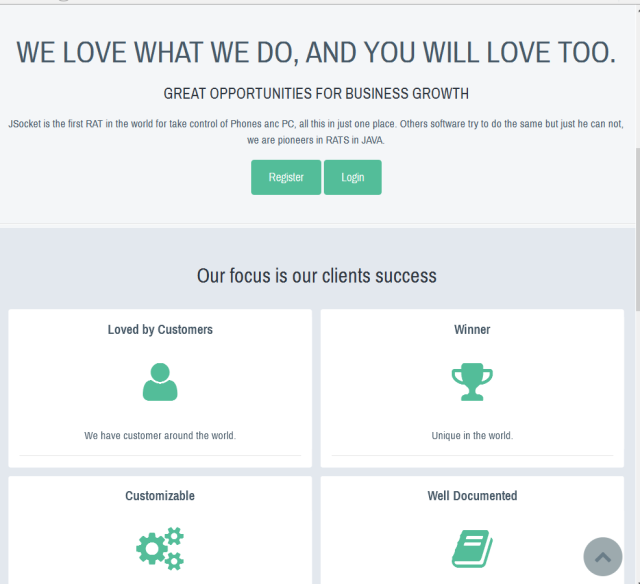
The JSocket website: open for business on the open Web (at least right now). (credit: Sean Gallagher)
A family of Java-based malware that has given attackers a backdoor into Windows, Linux, Mac OS X, and Android devices since 2013 has risen from the dead once again as a "commercial" backdoor-as-a-service. It was recently detected in an attack on a Singapore bank employee. Previously known as AlienSpy or Adawind, the malware was all but shut down in 2015 after the domains associated with its command and control network were suspended by GoDaddy. But according to Vitaly Kamluk, the director of Kaspersky Lab's Asia/Pacific research and analysis team, the malware has been modified, rebranded, and is open for service again to customers ranging from Nigerian scam operators to possible nation-state actors. Ars has confirmed that the service is offered openly through a website on the public Internet.
AlienSpy was found last spring on the Android phone of Alberto Nisman, the Argentinian prosecutor who died under suspicious circumstances just as he was apparently about to deliver a report implicating the Argentine government in the bombing of a Buenos Aires Jewish community center in 1994. Now resurrected under the names JSocket and jRat, according to a presentation by Kamluk at the Kaspersky Security Analyst Summit 2016 in Tenerife, the malware is available through an open website to subscribers at prices ranging from $30 for one month to $200 for an unlimited license. Kamluk believes the service's author is a native Spanish speaker, possibly based out of Mexico.
JSocket includes a number of typical "RAT" (remote access tool) capabilities, including video capture from webcams, audio capture from microphones, the ability to detect antivirus software on a system, a keylogger to record key strokes, and a virtual private network key-stealing feature that could be used to gain access to any of the VPNs used by the victim. Kaspersky has tracked more than 150 attack campaigns against more than 60,000 targets with the latest iterations of the malware, with Nigerian e-mail-based scam operations (particularly those targeting banks) being the biggest adopters of the tool. The lion's share of the remaining subscribers to the malware appeared to come from the US, Canada, Russia, and Turkey.