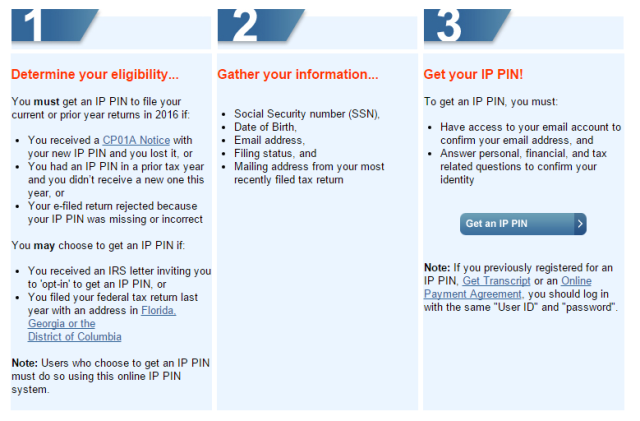
The Internal Revenue Service has temporarily suspended use of its Identity Protection PIN tool "as part of its ongoing security review," according to a notice issued by the IRS. The IP PIN is supposed to act as an extra layer of security for taxpayers who are at higher risk of becoming the victims of fraud because of personal information leaked in commercial data breaches.
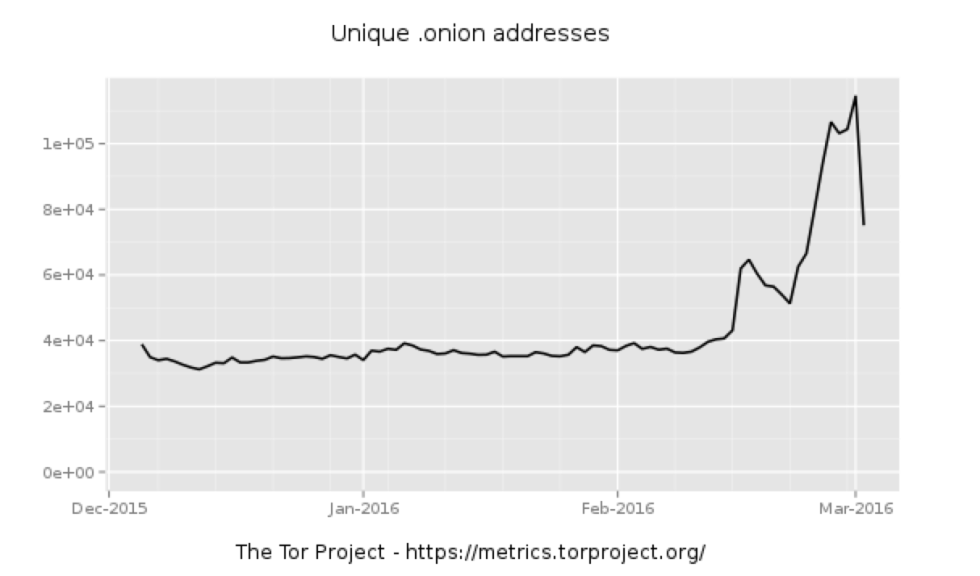
Last year, the IRS shut down an electronic tool for obtaining tax data after a massive fraud operation using stolen Social Security numbers and other data from commercial data breaches managed to extract filing data for hundreds of thousands of taxpayers. This year, the IRS is facing a new wave of fraud, as criminals engage in a phishing campaign to obtain employees' W-2 form data.
On March 1, the IRS issued a warning to human resources departments throughout the US about the wave of phishing attacks—e-mails purportedly from company CEOs directed to payroll or HR employees, usually with text such as: