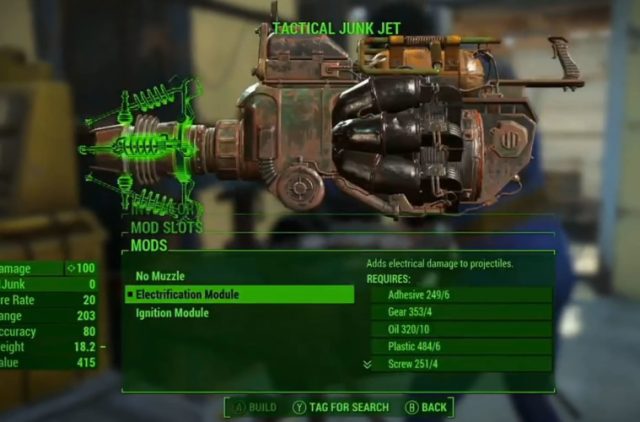
President Obama places a call from his secure BlackBerry 8900 from the presidential limo while in Indonesia in 2010. Secretary of State Clinton wanted similar phones for her staff, but they were told to "shut up and go color" by NSA. (credit: White House Photo by Pete Souza, November 10, 2010))
Judicial Watch, the conservative political action group that has largely driven the investigation into former Secretary of State Hillary Clinton's e-mails, has obtained documents through a Freedom of Information Act request indicating that Clinton tried and failed to get the National Security Agency to give her the same secure BlackBerry that President Obama used. Donald Reid, the State Department's coordinator for security infrastructure, reported in a 2009 e-mail, "Each time we asked the question 'What was the solution for POTUS,' we were politely asked to shut up and color."
Reid was trying to solve a problem for Assistant Secretary of State for Diplomatic Security Eric J. Boswell—the problem being that the new secretary of state was a certifiable BlackBerry addict but wasn't much of a computer user. Clinton became hooked on the BlackBerry in much the same way that President Obama did during the 2008 presidential campaign but found her preferred method of checking e-mail was banned from the secure office space at State's "Mahogany Row," the 7th floor at the State Department's Foggy Bottom headquarters in Washington. Use of wireless devices was banned in the space, which is designated as a Sensitive Compartmented Information Facility (SCIF).
But Reid found that using the desktop computer within the SCIF for e-mail was not in Clinton's comfort zone: