Dump exposes users’ private messages, IPs, e-mail addresses, and password data.
A website that openly facilitated the brokering of compromised passwords, stolen bitcoins, and other sensitive data has been hacked, exposing login data, IP addresses, e-mail addresses, purchase histories, and private messages for some 500,000 members.
Nulled.io, a hacker forum that used the tagline "expect the unexpected," was compromised earlier this month in a hack that exposed virtually all of the private data associated with it, security researchers said. As of publication time, more than a week later, the resulting 1.3 gigabyte compressed archive file remained available on a popular data breach sharing site on the clear Web. It was easily accessible to anyone, including hacking victims, fellow hackers, and law enforcement agents. The dump was discovered by analysis firm Risk Based Security and confirmed by Troy Hunt, operator of the have i been pwned? breach disclosure service.
"When services such as Nulled.io are compromised and data is leaked, often it exposes members who prefer to remain anonymous and hide behind screen names," the Risk Based Security blog post stated. "By simply searching by e-mail or IP addresses, it can become evident who might be behind various malicious deeds. As you can imagine, this can lead to significant problems for forum users."
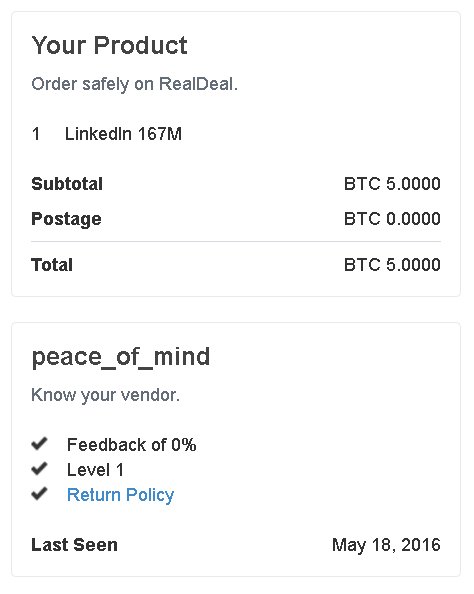
The leak provides a fly-on-the-wall account of the bartering that normally takes place only behind closed doors on criminal forums. In one exchange, two members discuss the trading of stolen Bitcoin and PayPal accounts and negotiate a profit share of 5 percent to 10 percent.
"Don't you make a fortune off Amazon Refunding? Lol," one user asks in the exchange. The action involves trading $250 worth of bitcoins for $250 in PayPal credit.
"I will when my bank is also out of negative balance m8 so I can get the full 250."
In a separate private discussion between two different members, one seeks software and technical support for installing a keylogger on a lab of an unnamed university. In a third conversation, one member seeks help cracking a Hotmail account. All of the discussions show the IP addresses the members used when making their comments. Assuming they correspond to traceable Internet accounts, the data could be used to reveal the real-world identities of the members.
The dump also includes e-mail addresses and password data for as many as 536,000 user accounts. The passwords appear to be protected by MD5, a hashing algorithm that's woefully inadequate for storing passwords because the underlying algorithm is so fast. The hashes observed by Hunt have cryptographic salts attached to them, so it's possible the MD5 hashes were iterated enough times to make mass cracking impractical. Either way, it's surprising that a hacking site that counseled users to expect the unexpected didn't rely on a more secure hashing function such as bcrypt or PBKDF2.
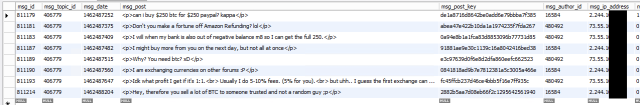
According to Risk Based Security, the dump also includes details of members' purchasing leaked content, stolen credentials, and pirated hacking software. The data cache contains discussions that took place in VIP forums, which allowed members a smaller, more intimate setting for trading stolen data and hacking techniques. In all, there are 2.2 million posts, 800,593 user personal messages, 5,582 purchase records, and 12,600 invoices. Company researchers said they also found credentials for the the site's PayPal, Bitcoin, and Paymentwall gateways and geolocation data linked to some users.
It's not clear precisely how Nulled.io was hacked, but the Risk Based Security researchers pointed out that the IP.board forum software and accompanying plugins the site relied on were riddled with critical vulnerabilities. They speculated that unknown hackers exploited the vulnerabilities to gain complete control to the site and then leaked the entire database. The breach is the latest reminder just how fragile privacy is on the Internet. It's likely that at least some Nulled.io users are now learning this lesson the hard way.