Enlarge (credit: Gerald England)
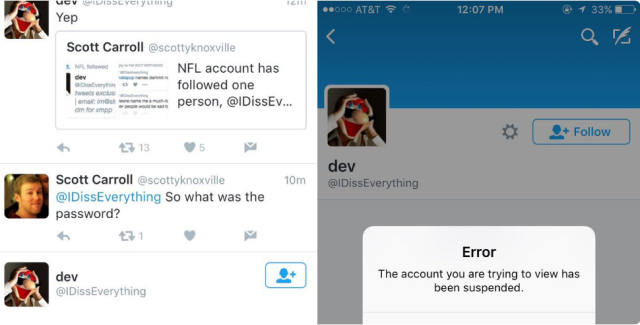
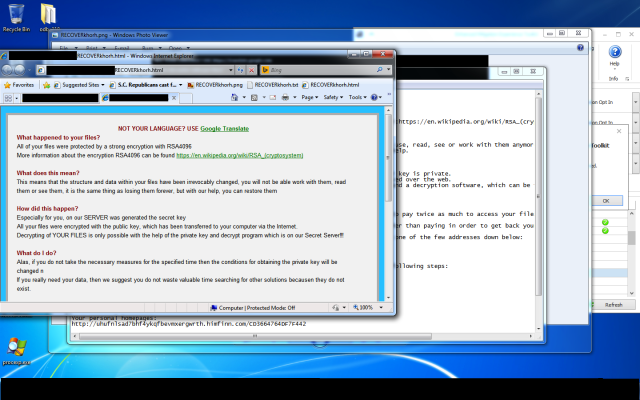
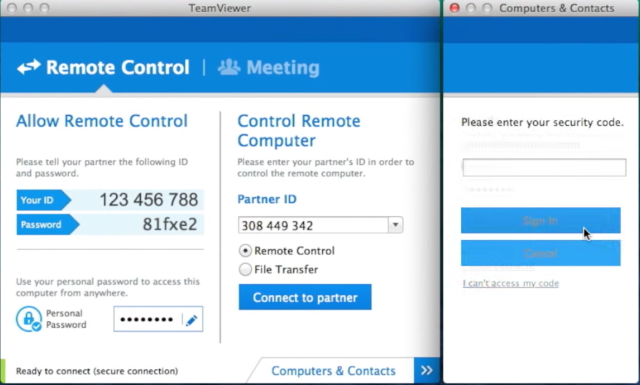
Underscoring the flourishing world of for-profit hacking, researchers have uncovered a thriving marketplace that sells access to more than 70,000 previously compromised servers, in some cases for as little as $6 apiece.
As of last month, the xDedic trading platform catalogued 70,624 servers, many belonging to government agencies or corporations from 173 countries, according to a report published Wednesday by researchers from antivirus provider Kaspersky Lab. That number was up from 55,000 servers in March, a sign that the marketplace operators carefully maintain and update the listed inventory.
"From government networks to corporations, from Web servers to databases, xDedic provides a marketplace for buyers to find anything," Kaspersky researchers wrote in a separate blog post. "And the best thing about it—it's cheap! Purchasing access to a server located in a European Union country government network can cost as little as $6." The post continued: