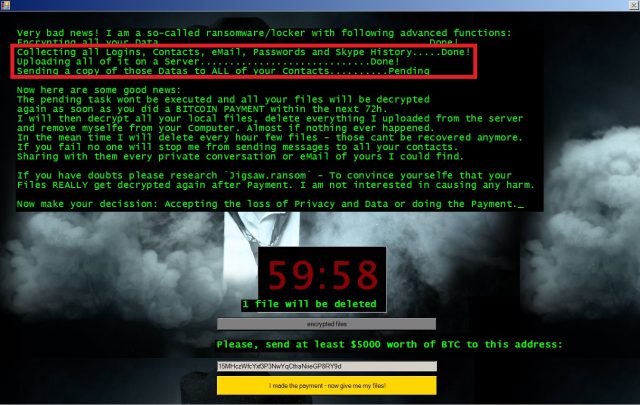
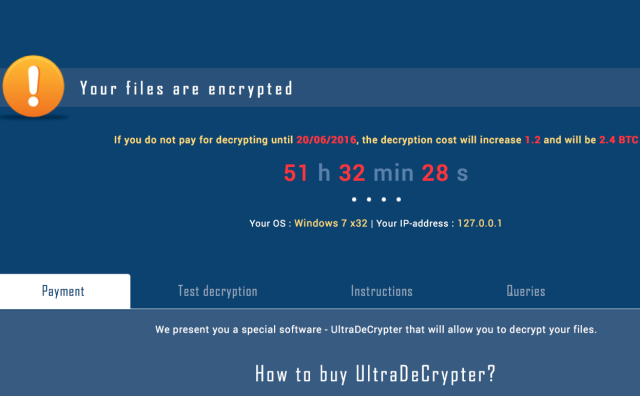
(credit: LPS.1)
Much of the product line from security firm Symantec contains a raft of vulnerabilities that expose millions of consumers, small businesses, and large organizations to self-replicating attacks that take complete control of their computers, a researcher warned Tuesday.
"These vulnerabilities are as bad as it gets," Tavis Ormandy, a researcher with Google's Project Zero, wrote in a blog post. "They don’t require any user interaction, they affect the default configuration, and the software runs at the highest privilege levels possible. In certain cases on Windows, vulnerable code is even loaded into the kernel, resulting in remote kernel memory corruption."
The post was published shortly after Symantec issued its own advisory, which listed 17 Symantec enterprise products and eight Norton consumer and small business products being affected. Ormandy warned that the vulnerability is unusually easy to exploit, allowing the exploits to spread virally from machine to machine over a targeted network, or potentially over the Internet at large. Ormandy continued: