(credit: The Intercept)
A secret catalog of cellphone spying gear has been leaked to The Intercept, reportedly by a person inside the intelligence community who is concerned about the growing militarization of domestic law enforcement.
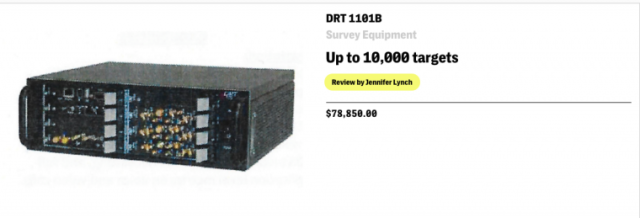
Among the 53 items are the now-familiar Stingray I/II surveillance boxes. They're billed as the "dragnet surveillance workhorse [that] has been deployed for years by numerous local law enforcement agencies across the United States." It has a range of 200 meters and sells for $134,000. A chief selling point is the "ready-made non-disclosure agreements from the FBI and Harris Corp. [that] will provide a pretext for concealing these features from the public." The listing also touts Harris' "next-generation Hailstorm, a must-have for cracking the 4G LTE network."
Besides manufacturing the Stingray brand of surveillance gear, Harris once employed a spokesman name Marc Raimondi. According to an Intercept article accompanying the leaked catalog, Raimondi is now a Department of Justice spokesman who says the agency's use of stingray equipment is legal.