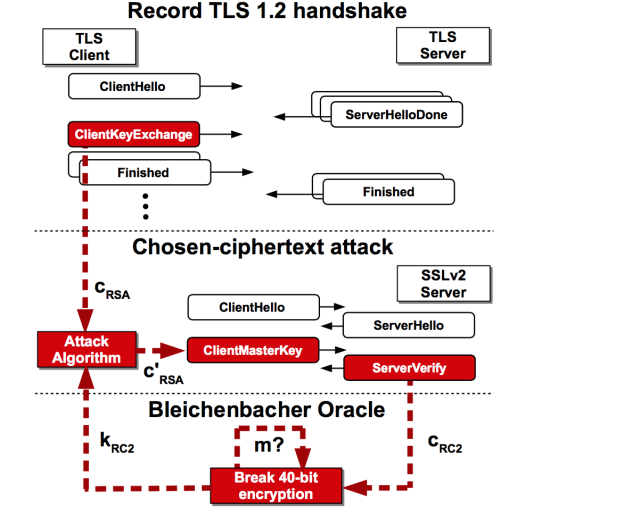
Enlarge (credit: Genkin et al.)
Researchers have devised an attack on Android and iOS devices that successfully steals cryptographic keys used to protect Bitcoin wallets, Apple Pay accounts, and other high-value assets.
The exploit is what cryptographers call a non-invasive side-channel attack. It works against the Elliptic Curve Digital Signature Algorithm, a crypto system that's widely used because it's faster than many other crypto systems. By placing a probe near a mobile device while it performs cryptographic operations, an attacker can measure enough electromagnetic emanations to fully extract the secret key that authenticates the end user's data or financial transactions. The same can be done using an adapter connected to the USB charging cable.
"An attacker can non-invasively measure these physical effects using a $2 magnetic probe held in proximity to the device, or an improvised USB adapter connected to the phone's USB cable, and a USB sound card," the researchers wrote in a blog post published Wednesday. "Using such measurements, we were able to fully extract secret signing keys from OpenSSL and CoreBitcoin running on iOS devices. We also showed partial key leakage from OpenSSL running on Android and from iOS's CommonCrypto."